
News & Updates
 |
News & Updates |
||||
| Home | About | Specification | Papers & Presentations | Events | FAQ | Contact Us | |||||
Dissecting the Odin ransomware campaignOdin ransomware, the latest spinoff of the Locky family, has a number of distinctive properties that are extensively analyzed in this security report. |
Breaking news has recently hit the headlines of IT security resources. Locky, one of the prevalent file-encrypting Trojans of 2016, has been revamped. Its new iteration dubbed Odin emerged that inherits a great deal of features from its forerunners but at the same time accommodates some unique traits. The common denominators shared across all the offending applications from this family include the distribution mode, the cryptosystems applied, as well as the look and feel of user interaction components. Some of the novel characteristics are on the surface � the updated infection now appends the .odin suffix to encoded files, and the documents with ransom instructions got new names. The ransomware makes it impossible to identify specific files as it renames them to gibberish strings of five blocks of 32 hexadecimal characters separated by colons. This routine turns a random personal document into something like D5CAB3Ad-4F89-9529-8ADB-C5BE02844105.odin. This entry, obviously, cannot be recognized as a particular file being sought. 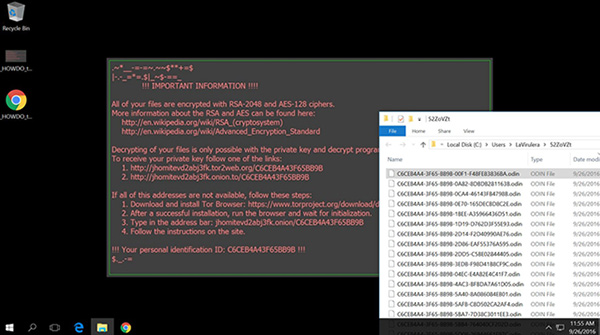
The way Odin infects Windows computers remains invariable. The ransomware operators rely on spam for this purpose, sending out thousands of rogue emails to users around the globe. Potential victims who double-click the attached WS or JS files run the risk of unknowingly executing the troublemaking DLL payload. Once the offending process runs on a PC, it starts with a scan for data. The hard drive, removable media and network shares are all subject to personal information lookup. All widespread types of files that it finds are then encrypted within minutes. This ransomware uses two algorithms to lock data, namely AES-128 and RSA-2048. To decrypt these personal files, the victim is instructed to send a ransom of 0.5 BTC, or approximately $300, to a specific Bitcoin address. To provide preliminary recovery steps, Odin replaces the desktop wallpaper with a warning image that contains a few Tor links. It also creates documents called _HOWDO_text.html and _HOWDO_text.bmp on the desktop, which hold the exact same set of directions. The linked-to resource titled the �Locky Decryptor Page� has the criminals� Bitcoin wallet details in it and supposedly makes the decrypt tool available as soon as the ransom payment is sent and verified. All in all, this is a well-orchestrated assault that performs the cyber extortion job immaculately. Given the rise of crypto ransomware these days, it�s strongly recommended to maintain secure backups of the most important files. Also, it�s more judicious than ever to exercise caution when dealing with spam email attachments. Do not enable macros in Microsoft Office documents, no matter how persuasive the corresponding prompts may appear. Furthermore, considering that some of these baddies can exploit software vulnerabilities to deposit their loaders, it�s imperative to update applications such as Adobe Flash Player and Java once new patches are released. |